DNS 投毒是 GFW 常用的一种屏蔽方法,今天在排查日志的过程中发现了 dajiaweibo.com 在 DNS投毒上有一点特殊之处,怀疑 GFW 可能启用了新的投毒方法,但并不能排除这是否是我个人或本地ISP的问题。因此在这里记录一下,希望能得到大家的帮助。
Ping检测
通过 chinaz 的测试,我们可以看出该域名已经被 DNS 投毒。
但这个域名的 DNS投毒与其它被投毒的域名有一点不一样。
先列出几个以往被投毒域名的测试结果。
~ % dig @example.com cmx.im AAAA ; <<>> DiG 9.14.2 <<>> @example.com cmx.im AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 29896 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;cmx.im. IN AAAA ;; ANSWER SECTION: cmx.im. 183 IN A 31.13.72.23 ;; Query time: 1586 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 22:46:09 CST 2019 ;; MSG SIZE rcvd: 40 ~ % dig @example.com cmx.im AAAA ; <<>> DiG 9.14.2 <<>> @example.com cmx.im AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 5442 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;cmx.im. IN AAAA ;; ANSWER SECTION: cmx.im. 100 IN A 31.13.72.17 ;; Query time: 531 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 22:46:12 CST 2019 ;; MSG SIZE rcvd: 40 ~ % dig @example.com www.google.com AAAA ; <<>> DiG 9.14.2 <<>> @example.com www.google.com AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 65128 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;www.google.com. IN AAAA ;; ANSWER SECTION: www.google.com. 220 IN A 31.13.68.22 ;; Query time: 40 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 22:46:26 CST 2019 ;; MSG SIZE rcvd: 48 ~ % dig @example.com www.google.com AAAA ; <<>> DiG 9.14.2 <<>> @example.com www.google.com AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58618 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;www.google.com. IN AAAA ;; ANSWER SECTION: www.google.com. 154 IN A 66.220.149.99 ;; Query time: 48 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 22:46:27 CST 2019 ;; MSG SIZE rcvd: 48 ~ % dig @example.com facebook.com AAAA ; <<>> DiG 9.14.2 <<>> @example.com facebook.com AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6778 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;facebook.com. IN AAAA ;; ANSWER SECTION: facebook.com. 169 IN A 69.171.247.71 ;; Query time: 52 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 22:46:36 CST 2019 ;; MSG SIZE rcvd: 46 ~ % dig @example.com facebook.com AAAA ; <<>> DiG 9.14.2 <<>> @example.com facebook.com AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 45509 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;facebook.com. IN AAAA ;; ANSWER SECTION: facebook.com. 212 IN A 69.171.237.16 ;; Query time: 47 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 22:46:37 CST 2019 ;; MSG SIZE rcvd: 46
以上是既往 GFW DNS投毒的测试结果,在之前的博文中已经有相关的介绍。
以下是 dajiaweibo.com 的测试结果,与上文对比可以看出明显的不同。
dajiaweibo.com 并没有返回一个虚假的 A记录。
~ % dig @example.com dajiaweibo.com AAAA ; <<>> DiG 9.14.2 <<>> @example.com dajiaweibo.com AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19227 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;dajiaweibo.com. IN AAAA ;; Query time: 34 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 18:57:17 CST 2019 ;; MSG SIZE rcvd: 43 ~ % dig @example.com dajiaweibo.com AAAA ; <<>> DiG 9.14.2 <<>> @example.com dajiaweibo.com AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21948 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;dajiaweibo.com. IN AAAA ;; Query time: 58 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 18:57:18 CST 2019 ;; MSG SIZE rcvd: 43 ~ % dig @example.com dajiaweibo.com AAAA ; <<>> DiG 9.14.2 <<>> @example.com dajiaweibo.com AAAA ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 12882 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;dajiaweibo.com. IN AAAA ;; Query time: 51 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 18:57:19 CST 2019 ;; MSG SIZE rcvd: 43
使用 Wireshark 进行抓包,可以看出对于当前AAAA请求,返回了一个空的DNS响应包。
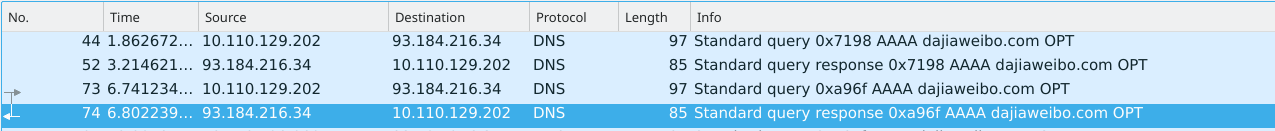
空的DNS响应包
~ % dig dajiaweibo.com AAAA +trace ; <<>> DiG 9.14.2 <<>> dajiaweibo.com AAAA +trace ;; global options: +cmd . 493554 IN NS e.root-servers.net. . 493554 IN NS b.root-servers.net. . 493554 IN NS d.root-servers.net. . 493554 IN NS h.root-servers.net. . 493554 IN NS l.root-servers.net. . 493554 IN NS m.root-servers.net. . 493554 IN NS j.root-servers.net. . 493554 IN NS c.root-servers.net. . 493554 IN NS i.root-servers.net. . 493554 IN NS a.root-servers.net. . 493554 IN NS g.root-servers.net. . 493554 IN NS f.root-servers.net. . 493554 IN NS k.root-servers.net. . 493554 IN RRSIG NS 8 0 518400 20190603050000 20190521040000 25266 . WloPJdtgUHKQLJ0DbSi8BLG5mCFRSPFvBrYIG9ALH+GbHUPFz/fzU+XU ixgWmjzlMkHrjBOOQXvBTq4AKNHe0eqSuxQy+Ne1BdfhlaYpzYbImsur ek4ohQdxnS1cwx+PajDyhfRg5pGWYWO+ilqqnMEkXzpWRGy/3a9Jbn1x fI7/0QcB39WRni8sB0YkNnJMi45LHD5QiYKGTrh8cd0SJlGNJvi+vHFQ rioNVD8BohU/uY1olLao8+HpCR/KEO0YI0mknIyc0WivwD3ljh8J/onO ciyKqv3PMZ7pRA3EF5CRVXkQATyCp2VTm1SjR2fJnGEZDb7EBzF4tBuR GfYV6A== ;; Received 1137 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms ;; expected opt record in response dajiaweibo.com. 182 IN A 74.86.228.110 ;; Received 48 bytes from 192.112.36.4#53(g.root-servers.net) in 1631 ms
但是奇怪的是:使用 dig +trace 却得到了虚假的A记录。
进一步探索后发现,加上 norecurse flag 之后,得到了虚假的A记录。
~ % dig @example.com dajiaweibo.com AAAA +norecurse ; <<>> DiG 9.14.2 <<>> @example.com dajiaweibo.com AAAA +norecurse ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34101 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;dajiaweibo.com. IN AAAA ;; ANSWER SECTION: dajiaweibo.com. 172 IN A 31.13.79.17 ;; Query time: 57 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 18:54:54 CST 2019 ;; MSG SIZE rcvd: 48 ~ % dig @example.com dajiaweibo.com AAAA +norecurse ; <<>> DiG 9.14.2 <<>> @example.com dajiaweibo.com AAAA +norecurse ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14697 ;; flags: qr aa; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;dajiaweibo.com. IN AAAA ;; ANSWER SECTION: dajiaweibo.com. 95 IN A 174.37.54.20 ;; Query time: 48 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 18:55:46 CST 2019 ;; MSG SIZE rcvd: 48 ~ % dig @example.com dajiaweibo.com AAAA +norecurse ; <<>> DiG 9.14.2 <<>> @example.com dajiaweibo.com AAAA +norecurse ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50409 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;dajiaweibo.com. IN AAAA ;; ANSWER SECTION: dajiaweibo.com. 127 IN A 31.13.64.1 ;; Query time: 111 msec ;; SERVER: 93.184.216.34#53(93.184.216.34) ;; WHEN: Tue May 21 18:55:47 CST 2019 ;; MSG SIZE rcvd: 48
抓包结果如下:

伪造的A记录
这到底是 GFW 升级了 DNS投毒方法,搞更精准的投毒?
还是这仅仅是我本地ISP的锅?
希望读到这里的朋友可以协助测试一下。